Unmanaged Applications
Visibility is everything. Even with application control, gaining a clear picture of the network is crucial. When overwhelmed by the amount of data they receive, IT administrators often create narrow blocklists and allowlists, applying policies to only frequently used applications. This results in something called a unmanaged applications omitted from both, which can open up risks in an organization, as network admins typically have little visibility over unmanaged applications.
As new applications get added, managing and securing networks becomes a challenge. The way to avoid this would be to create actionable policies encompassing all discovered applications to gain holistic visibility. To gain total control over the applications running in your organization, it's best to keep the number of applications in your unmanaged application at zero.
How do unmanaged applications affect productivity and security?
The two obvious approaches to deal with unmanaged applications is to either allow them to run or prohibit them from running. Enterprises that are keen on establishing the principle of Zero Trust usually block all unmanaged applications in order to have a tight grip over their network. While this helps with security, blocking unmanaged applications from running can cause serious chaos for IT teams.
IT administrators will be flooded with access requests every time an inadvertently defined allowlist policy is deployed. Additionally, all new applications installed will also be prohibited from running, as they would directly fall into the unmanaged. It's essential to strike the right balance between security and productivity when dealing with unmanaged application.
How does ManageEngine Application Control Plus deal with unmanaged application?
With flexibility modes like Audit Mode and Strict Mode, admins get a preview of how their network would function if they choose to run the applications currently in the unmanaged application. This enables them to make informed decisions before they enforce policies to add unmanaged applications to the blocklist.
Identifying and resolving unmanaged applications
- Tentative allowlists can be built and policies associating them with custom groups of users/systems can be deployed using Audit mode. This mode allows both allowlisted and unmanaged applications to run smoothly with simultaneous log collection.
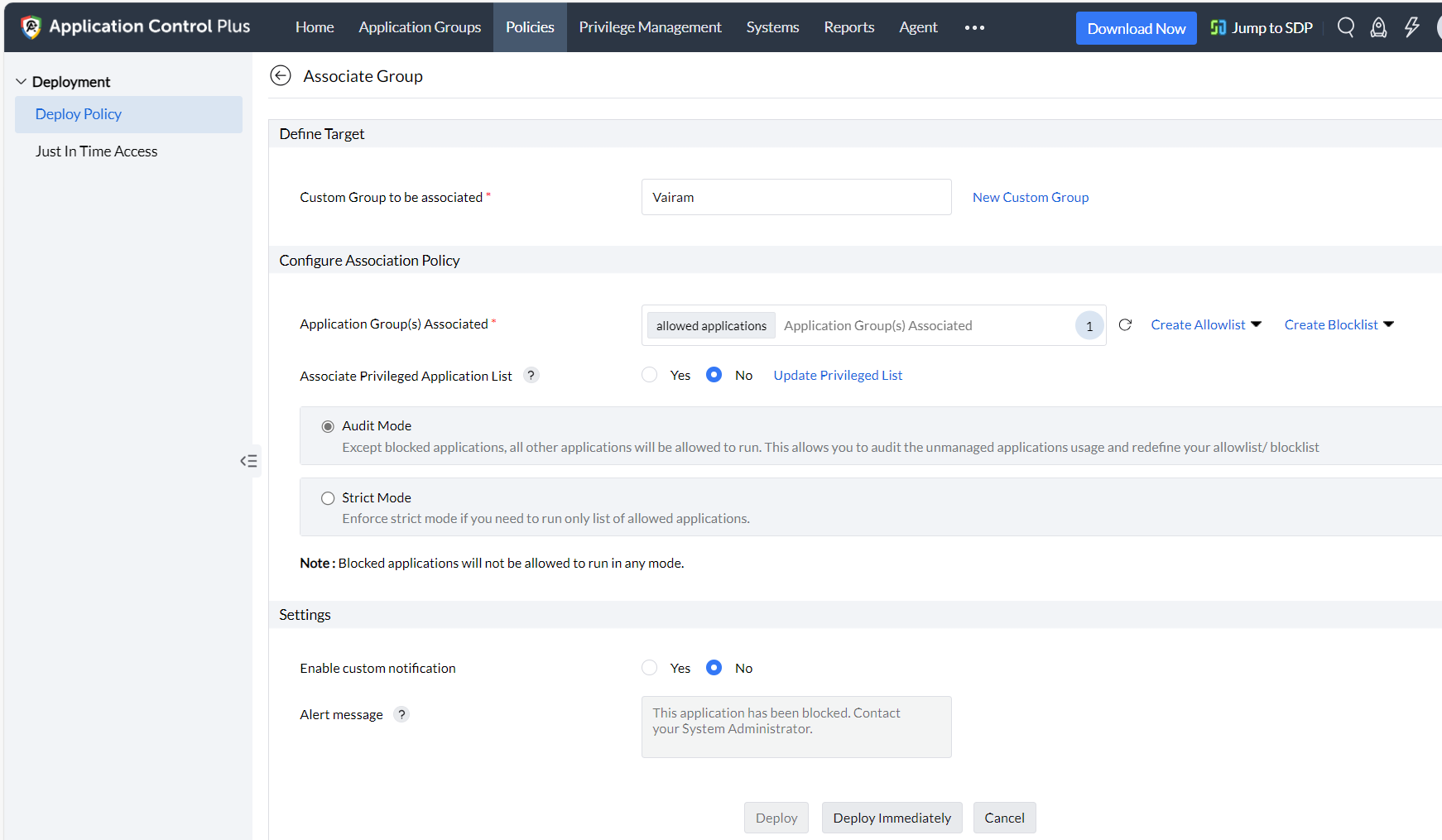
- After monitoring these logs for as long as needed, the IT administrators can resolve the unmanaged applications specific to a custom group. They can either be moved to a new or existing allowlist/blocklist depending on the frequency or legitimacy of their use.
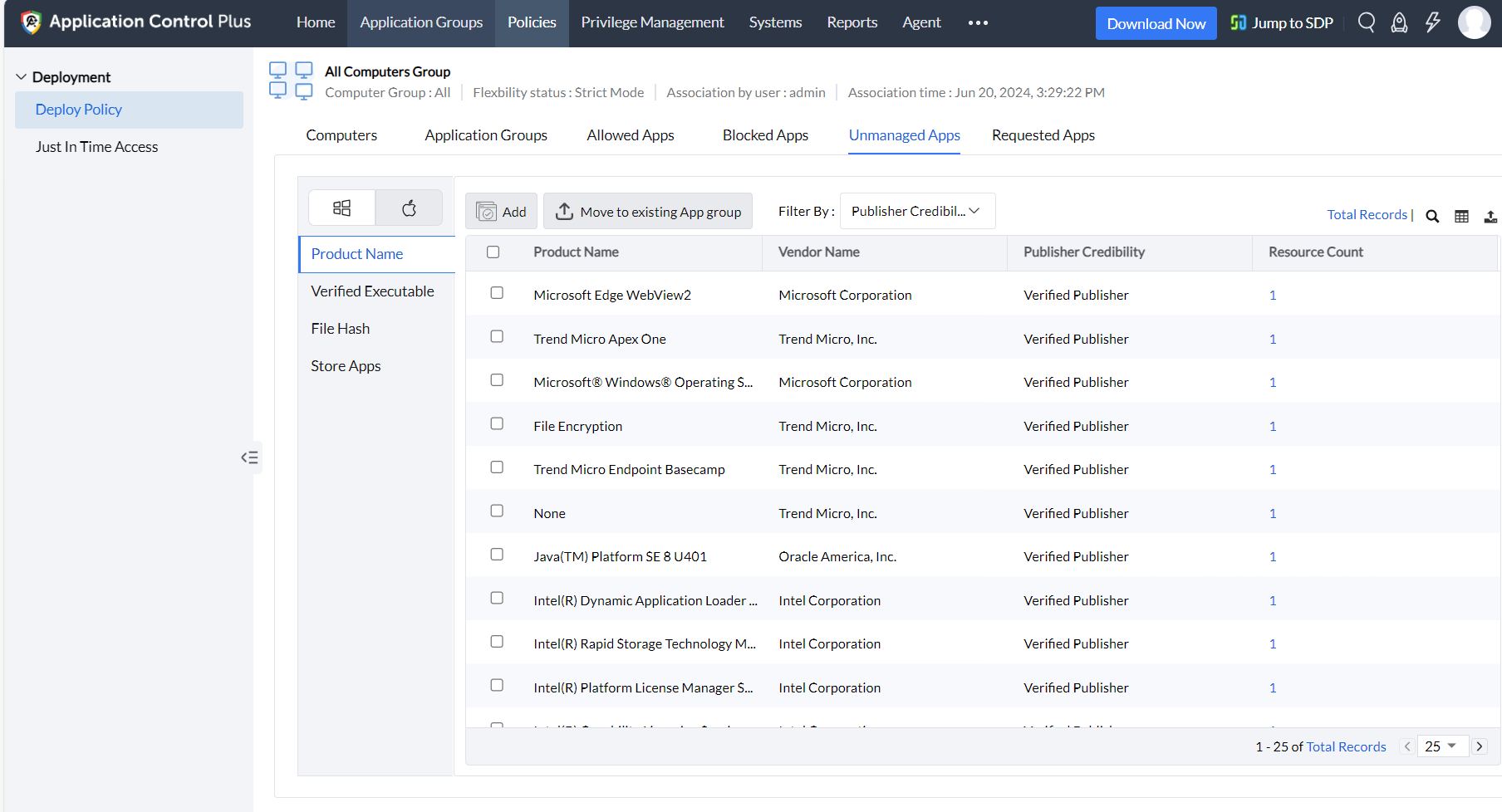
- Once the unmanaged application is resolved and the application allowlists are properly defined, the deployed policies can be modified to run in Strict Mode. This mode ensures heightened security as it only allows the allowlisted applications to run.
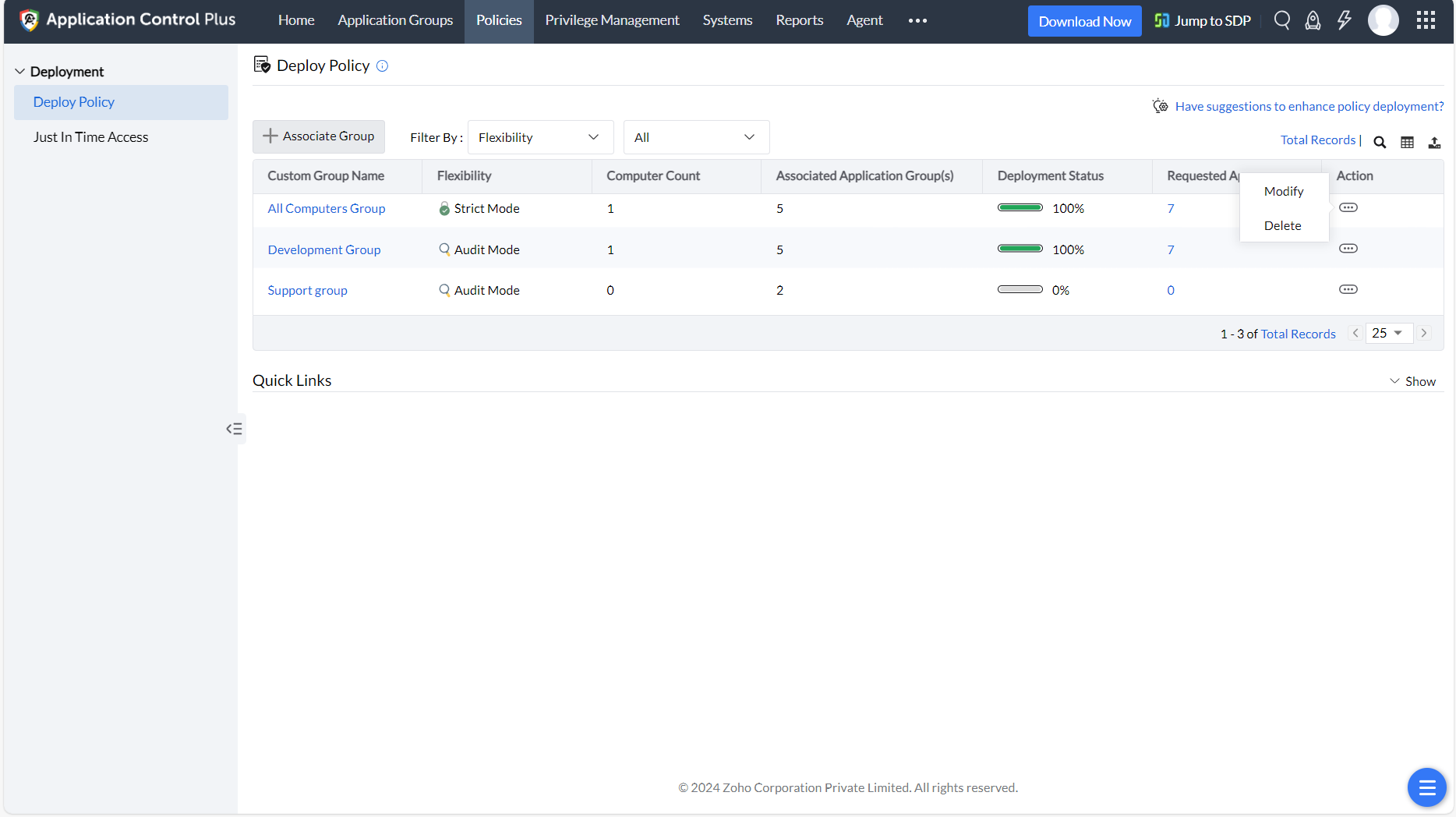
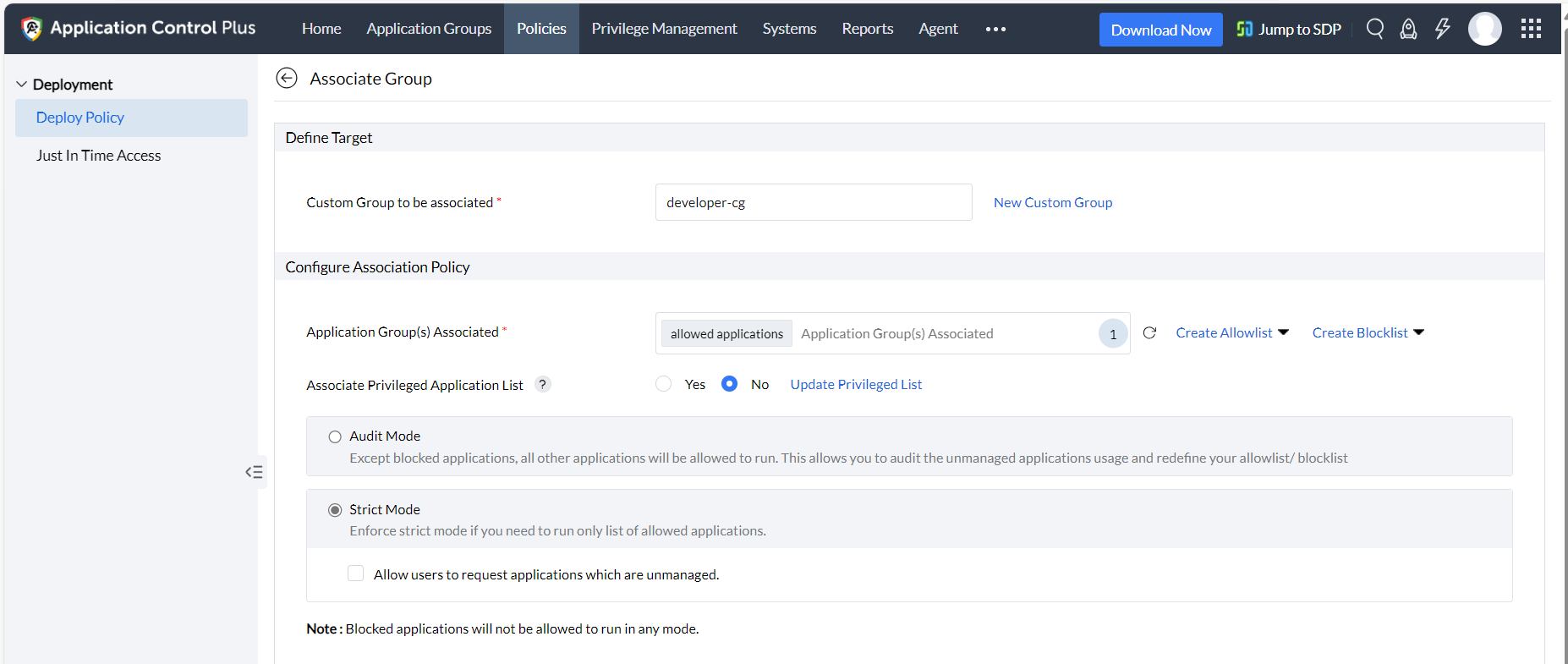
Even though having the enterprise unmanaged application count at zero is ideal, enterprises aiming to take a more relaxed approach with application control can continue to run their policies in Audit Mode combined with proper monitoring.
With Application Control Plus, taking control doesn't stop with allowlisting and blocklisting. Stay one step ahead by keeping tabs on unmanaged as well. Try Application Control Plus free for a trial period of 30 days!
